OUR GUARANTEE
IF IT IS NOT CLEANED UP IN 3 WORKING DAYS
(subject to any unforeseen circumstances)
THE LABOUR COMPONENT IS FREE!

Viruses and malware can slow your computer down, cause crashes and errors or in the worst case scenario steal information such as passwords without your knowledge which could cost you dearly.

Ransomware is becoming more prevalent. Suddenly out of the blue you get a message on the screen saying that your files (photos, documents, and data) have been “locked up” or “encrypted” behind a set of instructions stating that if you don’t pay a pre-determined fee to the hackers responsible in anywhere from 24 hours to a week, everything you hold near and dear will remain forever encrypted or deleted, never to be seen again.
Read more on ransomware on our web site under security.
Malware: Is malicious software that’s specifically developed to infiltrate or cause damage to computer systems without the owners knowing or their permission.
Let us carry out a THOROUGH virus and malware removal for you.
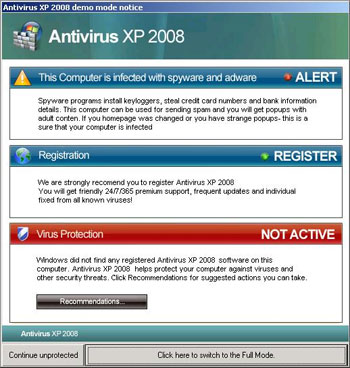
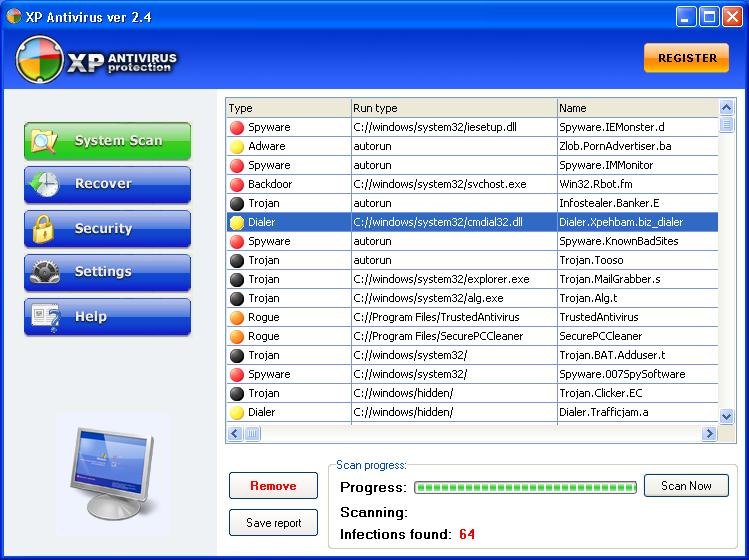
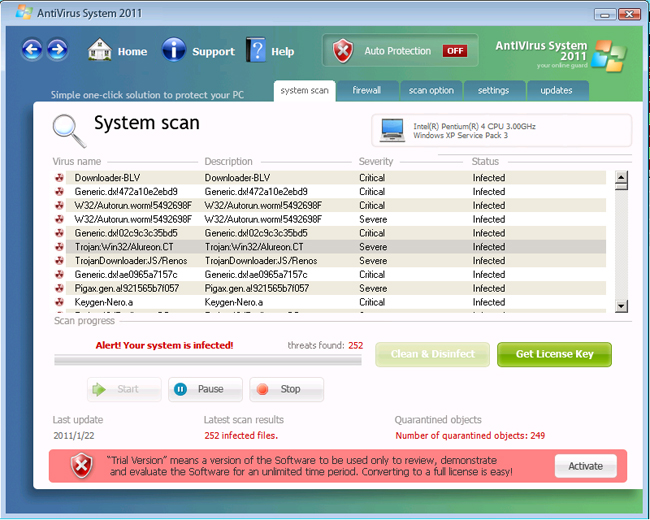
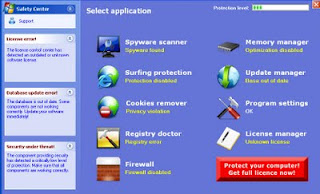
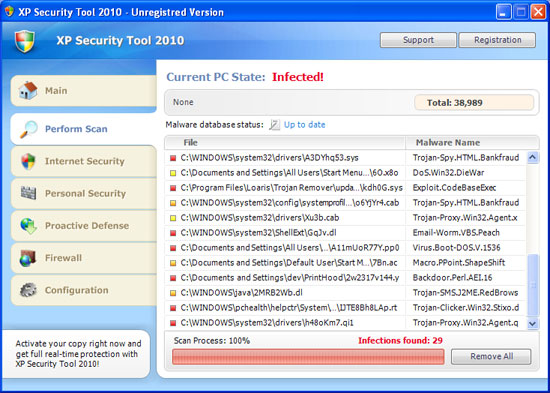
Fake anti-virus and security software is becoming a major threat. This is a form of computer malware that deceives or misleads you into paying for the fake or simulated removal of malware. It actually does nothing except take your hard earned money. To the inexperienced user it looks for all the world like legitimate software.
1: The infamous computer virus
A computer virus is malware that’s capable of infecting a computer but has to rely on some other means to propagate. A true virus can only spread from the infected computer to a non-infected computer by attaching to some form of executable code that’s passed between the two computers. For example, a virus could be hidden in a PDF file attached to an e-mail message.
2: The ever popular computer worm
Computer worms are more sophisticated than viruses, being able to replicate without user intervention. If the malware uses networks (Internet) to propagate it’s a worm rather than a virus.
3: The unknown backdoor
Backdoors are similar to the remote access programs that many of us use all the time. Once installed, back doors allow attackers complete remote control of the computer under attack. SubSeven, NetBus, Deep Throat, Back Orifice, and Bionet are backdoors that have gained notoriety.
4: The secretive trojan horse
“A trojan horse is a program that appears to have some useful or benign purpose, but really masks some hidden malicious functionality.”
Trojan horse malware cloaks the destructive payload during installation and program execution, preventing anti-malware from recognizing the malcode.
Vundo is a prime example; it creates pop up advertising for rogue anti-spyware programs, degrades system performance, and interferes with Web browsing.
5: Adware/Spyware, more than an annoyance
Adware is software that creates pop-up advertisements without the user’s permission. Typically the way adware gets installed is by being a component of free software. Besides being very irritating, adware can significantly decrease computer performance.
Spyware is software that collects information from your computer without your knowledge. Free software is notorious for having spyware as a payload, so reading the user agreement is very important.
6: Rootkits: Uniquely different
Rootkits are in a class all their own, choosing to modify the existing operating system instead of adding software at the application level like most malware. That’s significant, because it makes detection by anti-malware that much more difficult.
7: Blended threat
Malware is considered a blended threat when it seeks to maximize damage and propagate efficiently by combining several pieces of single-intentioned malcode. That said, blended threats deserve special mention as security experts grudgingly admit they’re the best at what they do